Estimated reading time: 2 minutes
With the recent issues with ransomware and the Wannacry attack, you really should now have SMBv1 disabled on your machines.
If you are still working on this or maybe not even started yet, then here we will show you a few examples of what to do to protect yourselves from future SMBv1 vulnerability and ransomware attacks.
Manual Commands
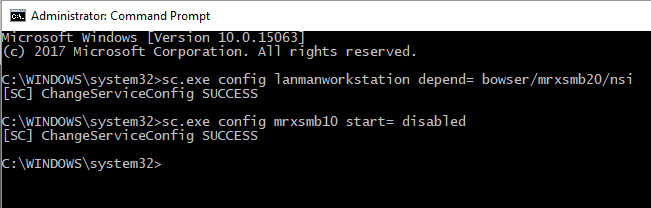
If you need to disable SMBv1 on just a few machines, then you may want to use a simple command line to start the services for SMBv1. To do this, run the following commands from an elevated command prompt:
sc.exe config lanmanworkstation depend= bowser/mrxsmb20/nsi sc.exe config mrxsmb10 start= disabled
So you should see something like this once complete:
Registry Edit
You can also make a registry change on a machine to disable the SMBv1 Protocol. To go this, go to the following registry location:
HKLMSYSTEMCurrentControlSetServicesLanmanServerParameters
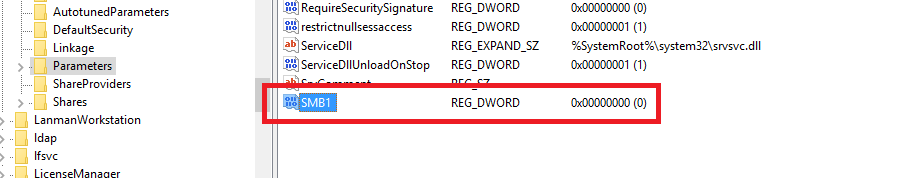
Then you need to add a DWORD with the following settings:
Name: SMB1
Value: 0
So it should look like this:
Reboot your machine for the changes to take affect.
Powershell
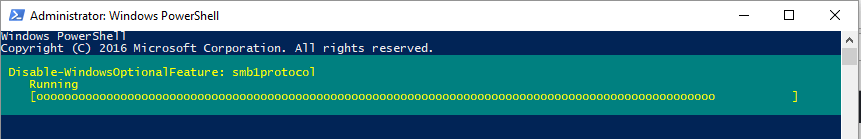
You can also run a Powershell command to uninstall the SMBv1 feature. To do this, open up a Powershell command box and enter the following command:
Disable-WindowsOptionalFeature -Online -FeatureName smb1protocol
This will then start the uninstall process:
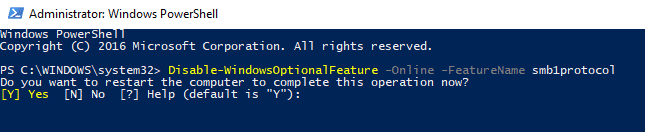
Once complete it will then ask you if you want to reboot your machine or not:
You can use all of the above methods to remove the SMBv1 vulnerbility on larger volumes of machines by using systems like Group Policy or Configuration Manager
Comments
If you have any questions or feedback on this guide, please feel free to leave us a message below.
Share this content:
Discover more from TechyGeeksHome
Subscribe to get the latest posts sent to your email.
